
Today we’re excited to announce the recent release of Wordfence CLI version 5.0.1 which includes a much requested feature from security analysts, hosting providers and ops teams: Database scanning for WordPress.
Now you can scan any WordPress database you have access to for malware and spamvertising with the new Wordfence CLI db-scan feature.
If you are managing many WordPress sites at the server level, the Wordfence CLI is a must-have. We’ve engineered it from the ground up to be blazingly fast, even if you’re scanning hundreds to thousands of sites at a time.
With release 5.0.1 we’ve added full database scanning capabilities to allow you to detect malicious code, spamvertising, and some common signs of compromise in your WordPress files and databases across entire servers.
We’ve released this feature with a free set of rules for all users and will add more over time.
Get Started With Wordfence CLI Version 5.0.1 Here
How To Start A Database Scan In Wordfence CLI
Watch this quick tutorial, created by David Nuzik from our Software Quality Assurance team, to learn about the new database scanning feature and how to use it.
Wordfence CLI Database Scanning Options
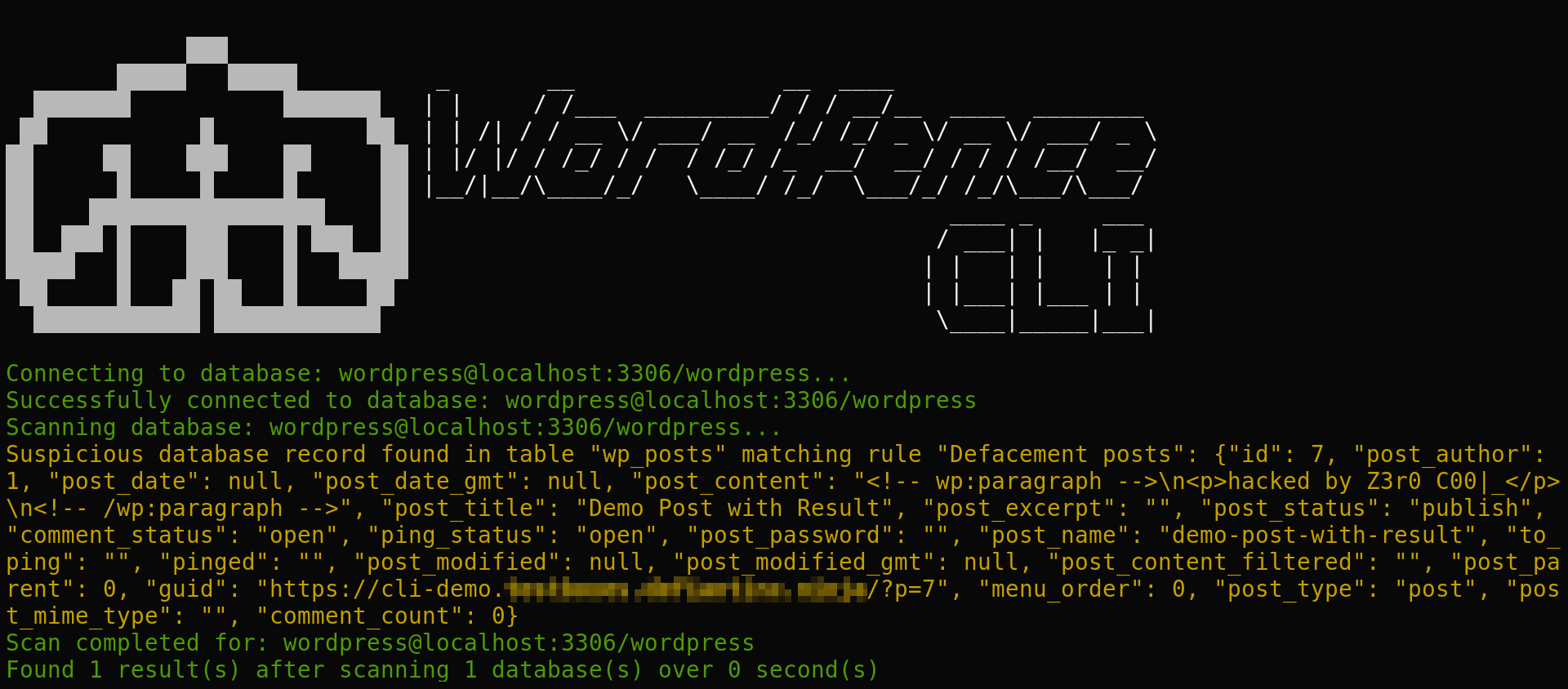
Wordfence CLI Databasse Scanning Results
Scan By Path With -S Flag
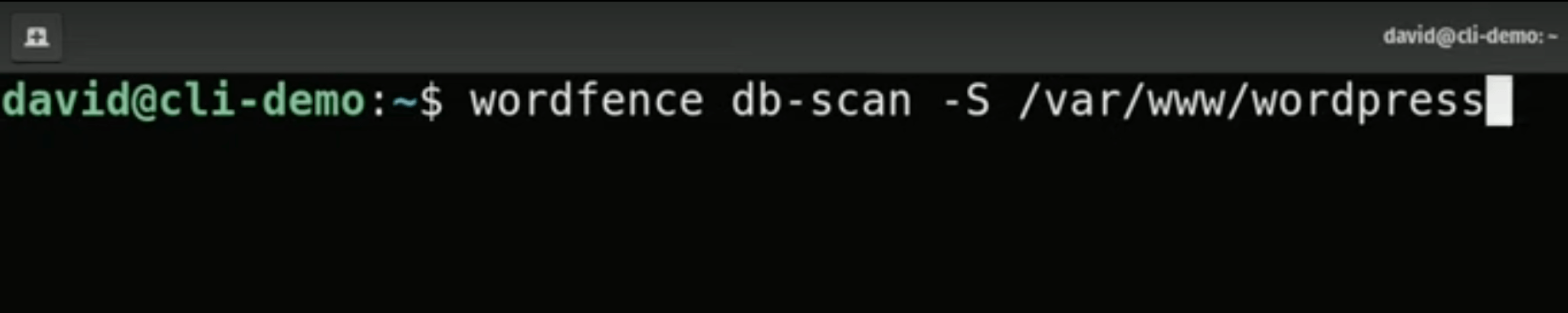
Easily scan any WordPress database by specifying the -S flag and WordPress path
Example: wordfence db-scan -S /var/www/wordpress
The rules define content to search for in specific WordPress database tables that may identify malicious code or compromise.
You may also scan any WordPress database by specifying the necessary connectivity information.
wordfence db-scan --help will list all database connectivity options.
Example:
wordfence db-scan -u dbuser -H myhost.example.xyz -D database_name -P 13306 --prefix wordpress_ --prompt-for-password
Run Via Cron Job Or Script
Wordfence CLI can be run via a cron job or script by leveraging the option to pass the password via environment variable.
Example:
# Example cron job running daily at 2 AM
0 2 * * * www-data . /home/www-data/.wfcli_env && wordfence db-scan -u dbuser -D wordpress
Other Subcommands
Use other features available with most other subcommands such as outputting a scan report to list any results found and/or emailing scan results.
Example:
wordfence db-scan -u dbuser -D wordpress --output-path /tmp/results.csv -m csv --output-headers -E admin@example.xyz
Other Changes In Wordfence CLI 5.0.1:
- Implemented database scanning
- Fixed error about mixed bytes and non-bytes in path components when pre-compiling vectorscan DB
- Added python3-mysqlclient dependency to RPM build
- Corrected pip command
- Replaced mysql-connector-python with mysqlclient
- Switched from mysqlclient to PyMySQL
- Added dbscan modules to pyinstaller
- Corrected property name
- Corrected handling of database prefix
- Corrected various typos and made adjustments per QA feedback
- Corrected casing of package dependency for RPM build
- Prevented errors from timer when no time has been measured
View the full changelog on github here.
Try Wordfence CLI 5.0.1 Today For Free
This incredible new feature furthers our goal of securing the web by empowering system administrators, hosting companies and other IT professionals with the full power of Wordfence at your fingertips from the command line.
If you’re excited to get started scanning today, try out Wordfence CLI for free.
The post WordPress Database Scanning For Malware Released in Wordfence CLI 5.0.1 appeared first on Wordfence.
