The Wordfence team is excited to announce the official launch of the Wordfence Vulnerability Management Portal, the latest addition to the Wordfence Intelligence suite. This new interface is designed to improve and simplify the vulnerability disclosure process between the Wordfence team and WordPress software vendors.
Over the past two years, Wordfence has expanded its Wordfence Intelligence offerings to include a vulnerability database, free API and webhook integrations, a Bug Bounty Program, and now the new Vulnerability Management Portal.
Our mission with Wordfence Intelligence has been to make vulnerability information free and accessible to the WordPress community and other security vendors. This mission has quickly evolved into creating the most rewarding Bug Bounty Program in the WordPress ecosystem, allowing us to attract top-tier research and provide Wordfence users with the best protection for WordPress. Now, we are expanding this by offering the best vulnerability management portal for vendors completely for free.
What makes the announcement of this portal particularly exciting is that the Wordfence team has already onboarded over 130 WordPress software vendors, covering over 640 unique pieces of WordPress software. This rapid adoption is incredibly exciting, especially considering that we’ve been operating in an exclusive, invite-only soft-launch period since June 1st, 2025.
The enthusiasm and participation from the vendor community have exceeded our expectations, demonstrating a clear need for a centralized, efficient vulnerability management solution within the WordPress ecosystem and with Wordfence’s rate of new vulnerability disclosures.
We are immensely eager to witness the continued growth of this program and the tangible improvements in the efficiency and reliability of responsibly disclosing vulnerabilities as more vendors join and integrate their processes. This collaborative effort will undoubtedly lead to a stronger, more secure WordPress environment for everyone.
Why We Launched the Vulnerability Management Portal for Vendors: Responsible Disclosure Critical in Vulnerability Management
Efficiency is Key for Quick Remediation
Responsible disclosure of newly discovered vulnerabilities is a top priority for Wordfence. In processing thousands of vulnerabilities per year, we found that we could serve WordPress vendors and the WordPress community even better by creating a dedicated and streamlined vendor management platform – leading to faster and easier vulnerability disclosures. This is one key reason behind the creation of the Wordfence Vulnerability Management Portal.
We also wanted to ensure that the portal remains accessible to all WordPress software vendors with zero obligations. This means you do not have to route all your vulnerabilities through Wordfence to leverage our vulnerability management portal.
While some vendors may require directing all vulnerability reports through them to benefit from a centralized portal for responsible disclosure, we opted to make that an optional step so that the best vulnerability management portal in the industry is accessible to all with minimal obligations. Vendors are welcome to leverage our portal to set up a Vulnerability Disclosure Policy (VDP), but that is not a requirement to leverage our new efficient disclosure process through the vulnerability management portal.
It’s Our Responsibility
At Wordfence, we are aware of our role as a leading security vendor and the highest quality vulnerability data provider. We process and disclose thousands of vulnerabilities annually though our Bug Bounty Program, and with that comes a profound responsibility. We believe that providing a straightforward, efficient, and streamlined means for responsible disclosure is not just a best practice, but a fundamental obligation.
Our commitment extends to fostering an environment where security researchers, developers, and the broader WordPress community can easily contribute to the collective security of the platform. We strive to make the vulnerability reporting process as accessible and clear as possible, ensuring that every reported vulnerability is handled with the utmost care, diligence, and respect. This dedication to responsible disclosure is a cornerstone of our efforts to protect the WordPress ecosystem and its millions of users.
While we encourage vendors to sign up for the vendor portal to streamline disclosure of new vulnerabilities reported by Wordfence, it is not a requirement of responsible disclosure, and we will still send disclosure details via other approved methods provided from organizations, granted it is a direct line of communication.
Benefits of the Wordfence Vulnerability Management Portal for Vendors
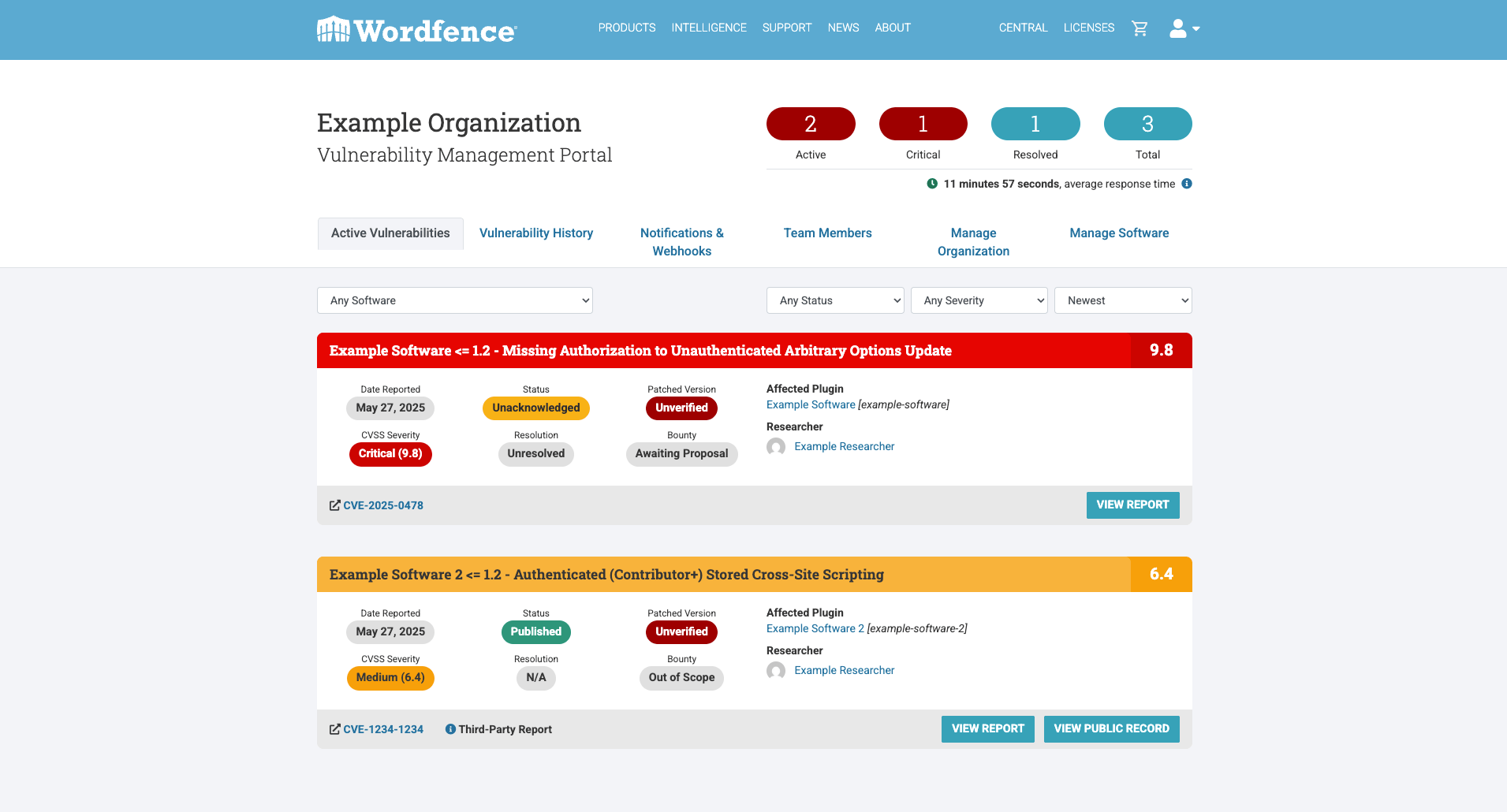
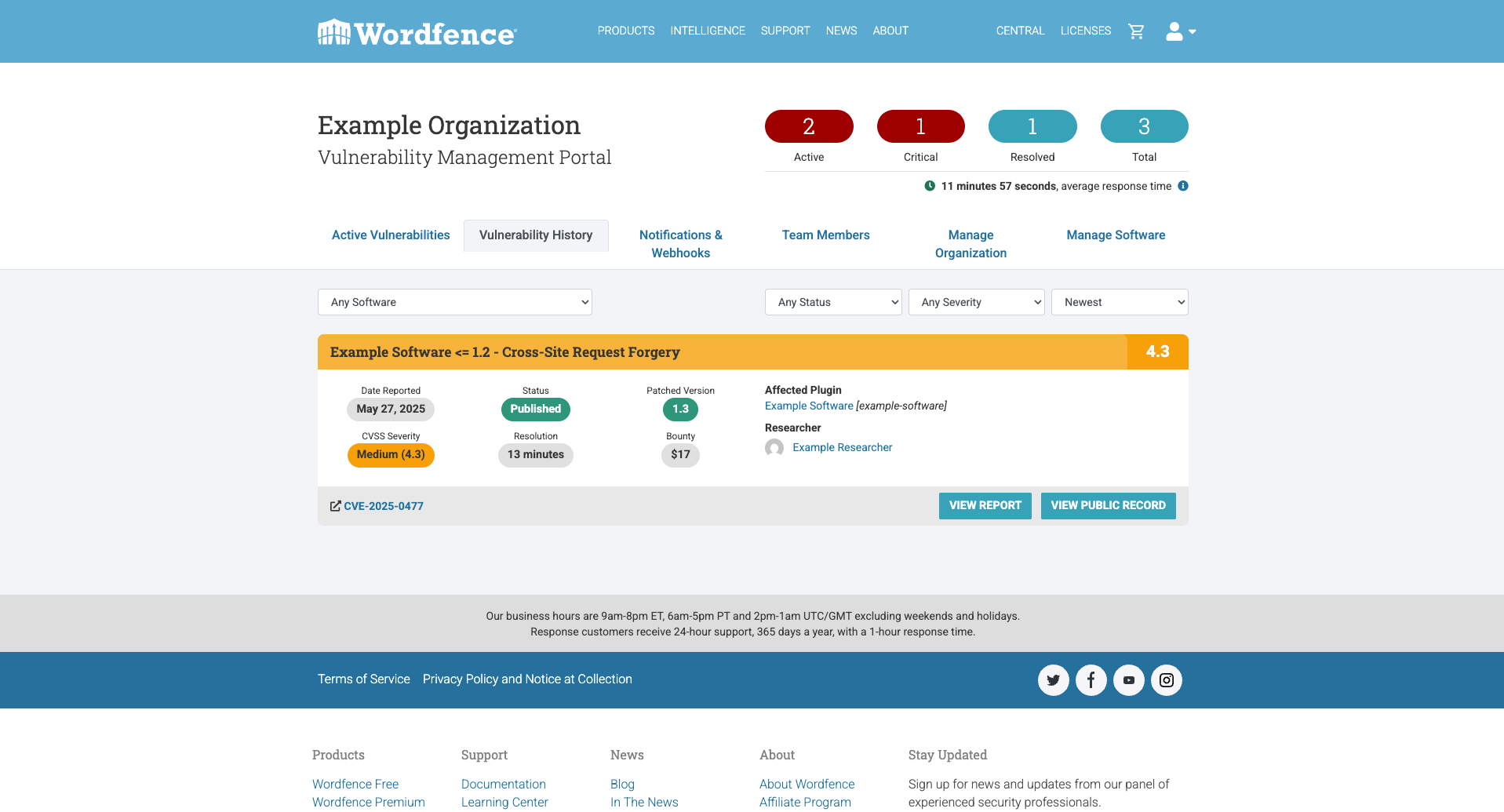
Centralized Dashboard for Active Vulnerability Submissions
Our new portal offers a centralized dashboard that provides a comprehensive overview of all active vulnerabilities in an organization’s software. This unified view simplifies the tracking and management of disclosed vulnerabilities, ensuring vendors have immediate access to the status of each vulnerability from needing acknowledgement to patch submissions being approved.
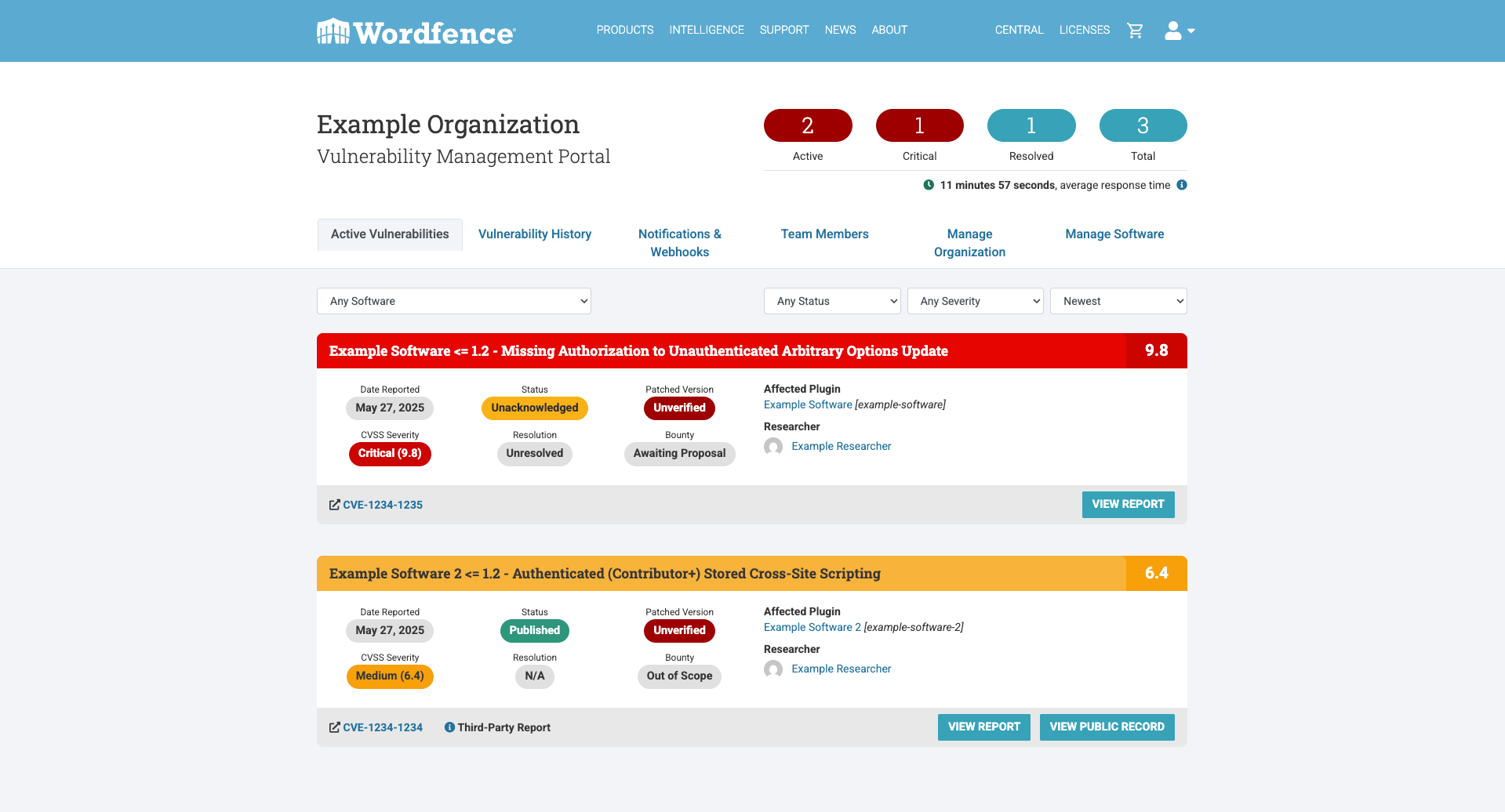
Detailed & Actionable Vulnerability Reports for New Disclosures
Technical Details
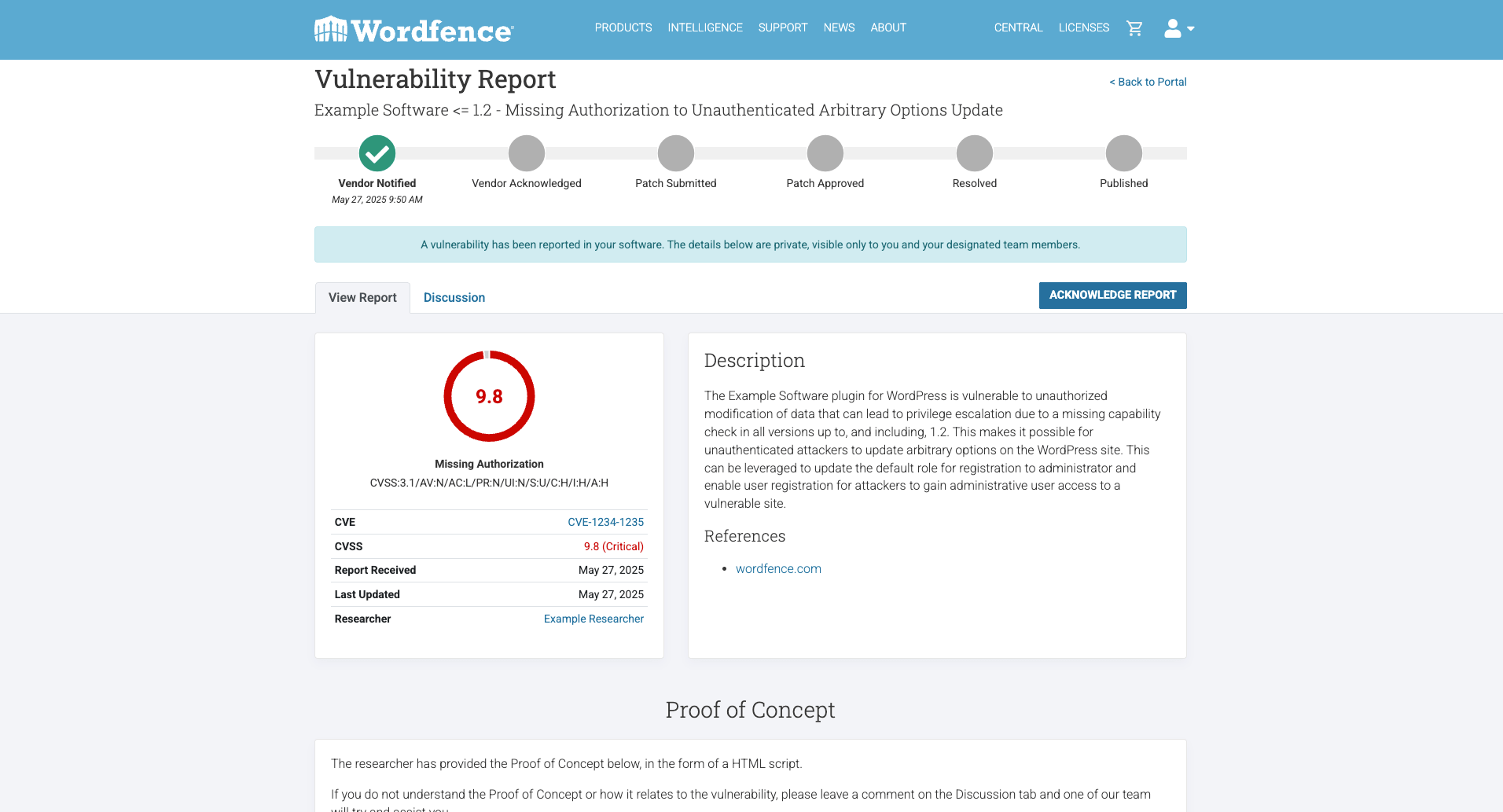
When a new vulnerability is discovered and validated by our team, the vulnerability management portal provides a comprehensive report. This report includes critical information such as the affected plugin/theme name, affected version numbers, vulnerability type, and a detailed description of the flaw.
We also include a severity score based on the CVSS (Common Vulnerability Scoring System) to help vendors prioritize their response. Furthermore, our reports will include proof-of-concept (PoC) code or steps to reproduce the vulnerability along with a recommended resolution, allowing vendors to quickly understand and replicate the issue for effective patching.
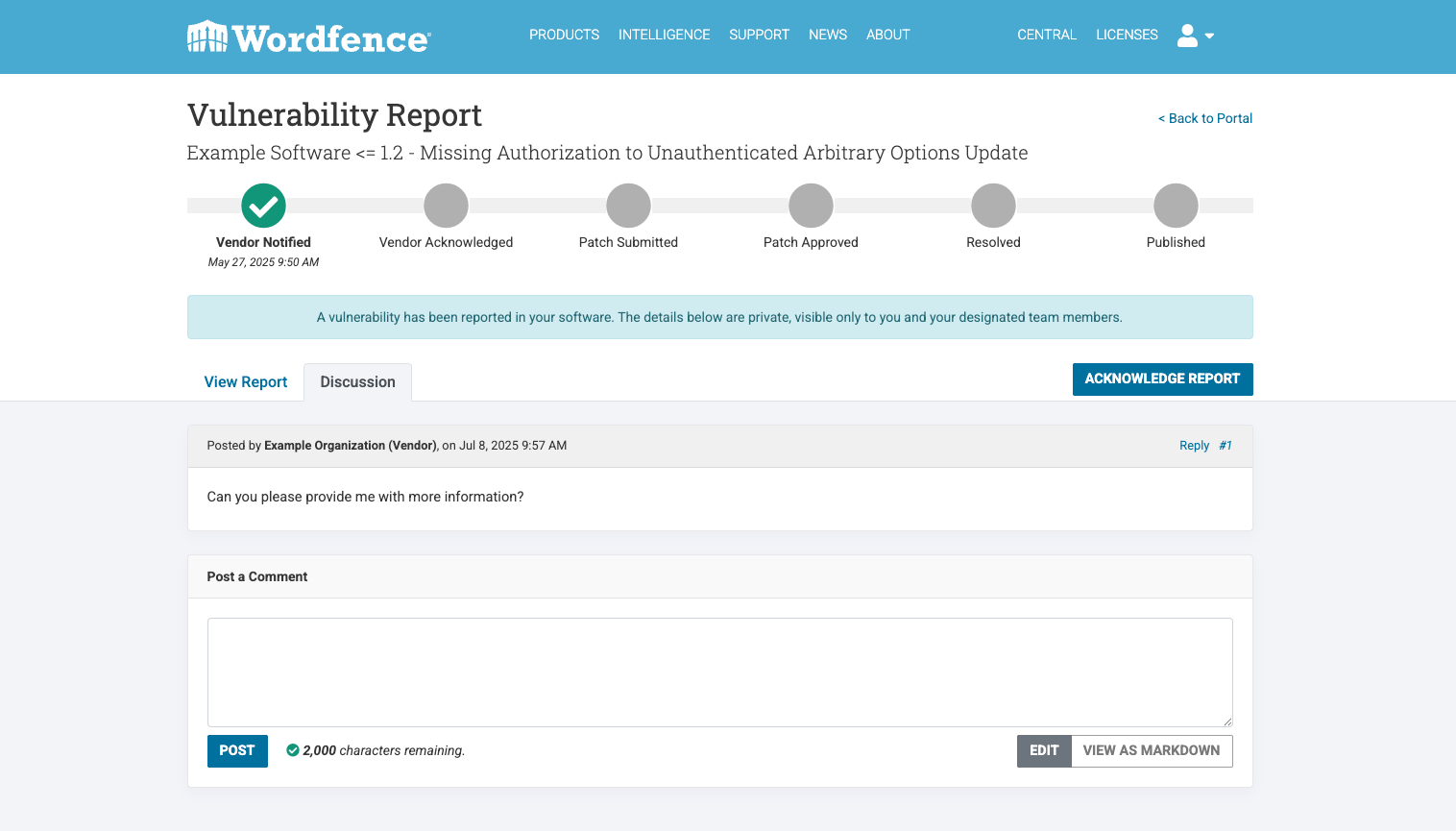
Discussion Area
Each report also provides a discussion tab for vendors to communicate directly with our team. This is an area where vendors can ask our team questions or we can ask the vendors questions about specific vulnerabilities.
Patch Management
The portal makes it possible for vendors to upload patches for review by our team, both before and after public release. This enhanced functionality facilitates improved interaction and more thorough patch assessments for vendors.
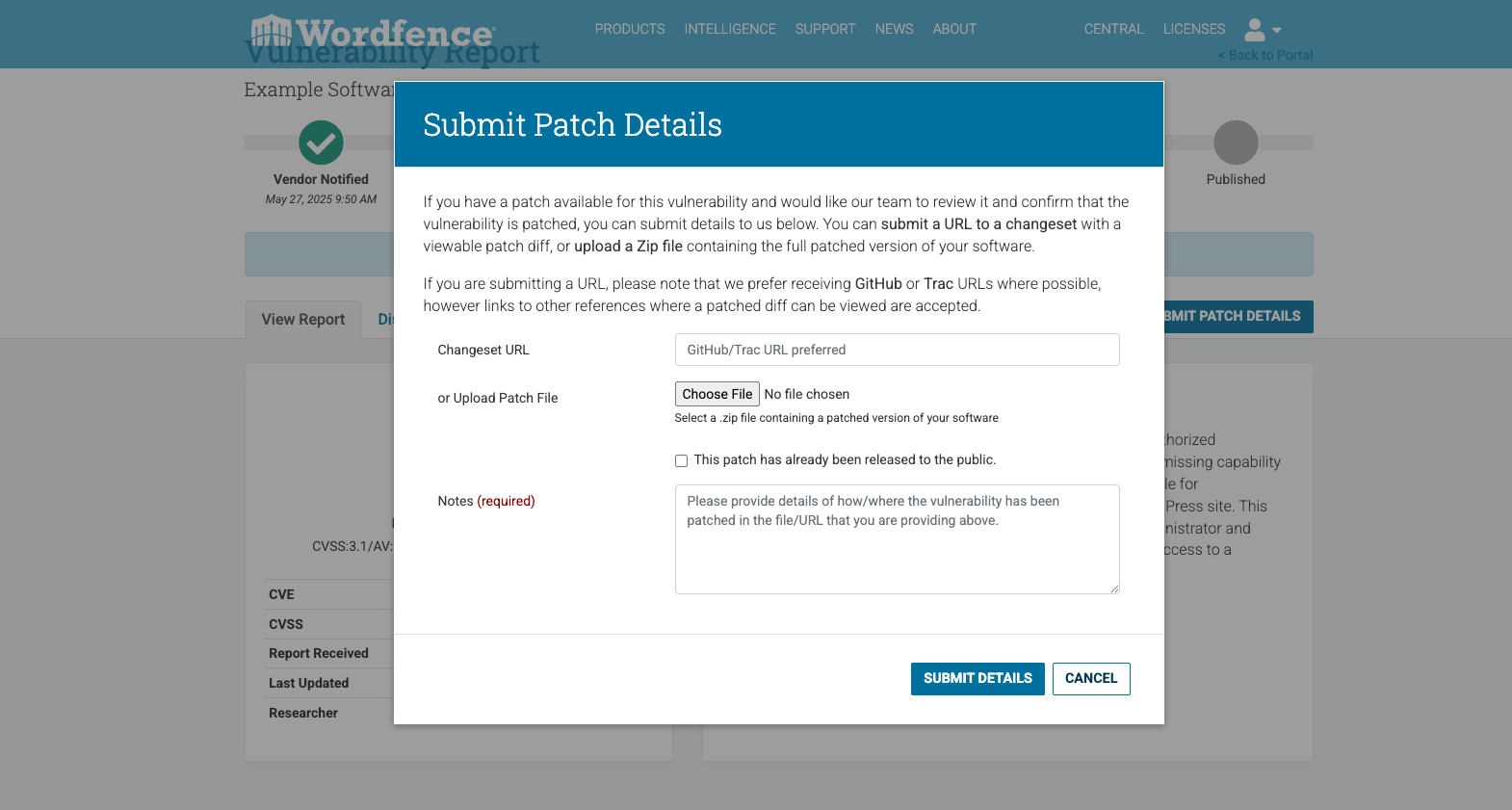
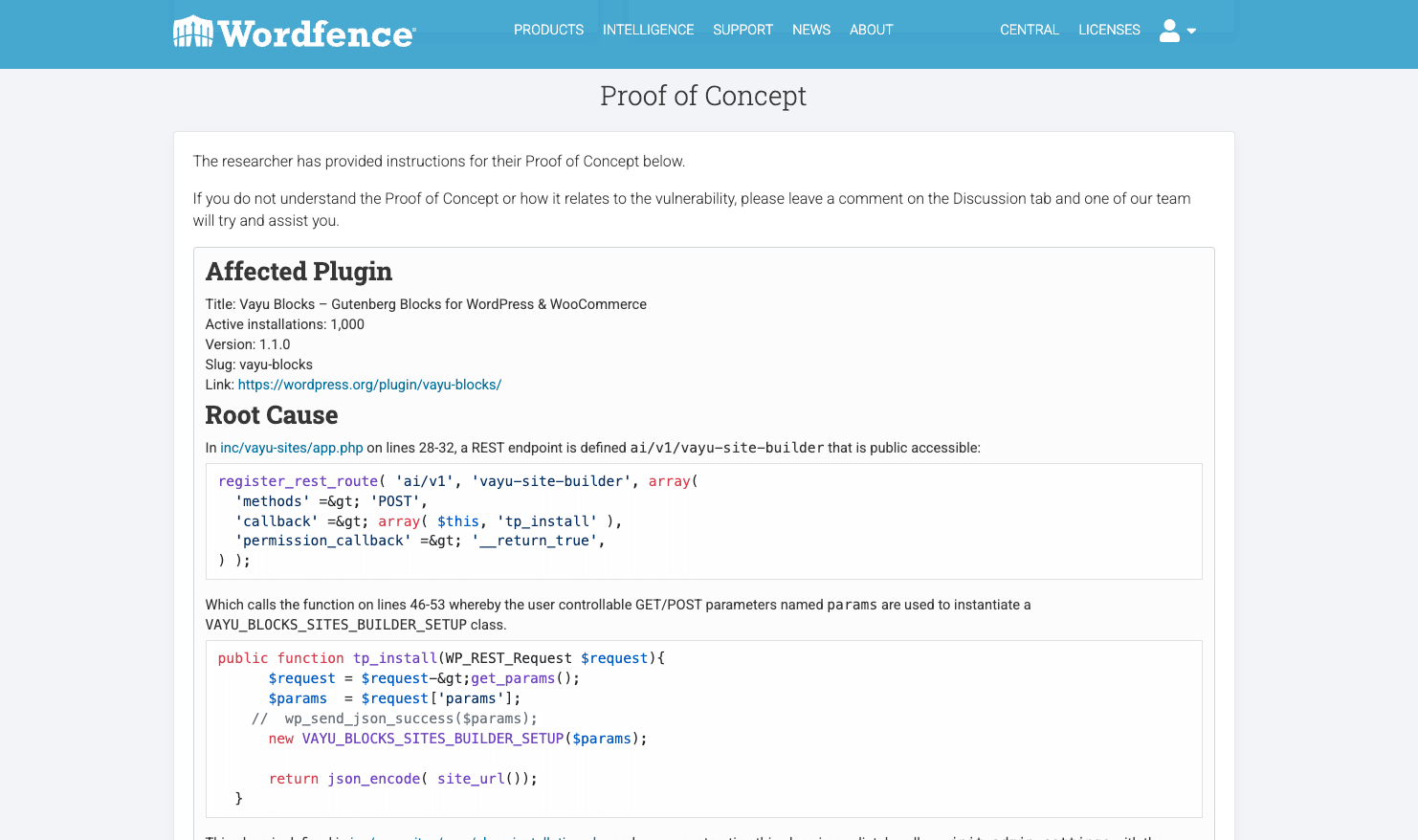
Markdown Support
We’ve ensured our vulnerability reports are enhanced with full Markdown support in the Proof of Concept, Recommended Solution, and vendor discussion board sections. This significantly improves readability and clarity, streamlining communication for complex technical details like code snippets and step-by-step instructions. Researchers and our team already use Markdown for efficient formatting, and now it’s natively supported in reports instead of broken down in email communications. This means:
- Proof of Concept sections can have detailed code blocks, lists, and bolded elements for easier replication.
- Recommended Solution sections can offer clearer, step-by-step guidance with lists and distinct formatting.
- Vendor discussion boards will have richer, more organized technical discussions.
This integration fosters a more efficient and user-friendly vulnerability disclosure process, reducing misinterpretations and speeding up resolutions.
Unpatched Published Vulnerability Alerts
In response to an alarming trend of unpatched vulnerabilities being published within the WordPress ecosystem, which you can learn more about in this report, we have developed a robust reporting and notification system for unpatched vulnerabilities. This system automatically generates a report in the portal when an unpatched vulnerability in a vendor’s software is publicly disclosed and added to the Wordfence Intelligence Vulnerability Database. This ensures that vendors registered for our portal will become immediately aware when an unpatched vulnerability has been published in their software so they can take quick action to remediate it.
Vendors can then use this report to notify us once a patch has been released, ensuring timely communication and resolution within our database used to alert millions of users to new vulnerabilities. This crucial feature empowers vendors to remain proactive and informed, allowing them to address vulnerability reports from third parties before they escalate.
Historical Vulnerability Archive including All Known Published Vulnerabilities
As part of the vulnerability management portal, vendors can view a historical archive of all vulnerabilities in any software under their ownership that have been published in the Wordfence Intelligence Vulnerability Database, along with any vulnerabilities that are actively undergoing disclosure through Wordfence. This includes vulnerabilities not just disclosed or discovered by Wordfence, but any across the entire internet that Wordfence has found and added to the database.
This comprehensive archive offers WordPress vendors an unparalleled advantage by providing a centralized, exhaustive view of past and ongoing vulnerabilities. It helps them proactively address security issues, understand historical patterns of vulnerabilities, and demonstrate a commitment to security by easily tracking their remediation efforts.
This visibility is crucial for strengthening their security posture within the WordPress ecosystem and maintaining trust with their users.
Vendors will also have access to see the bounty reward that Wordfence has awarded to a researcher for any particular in-scope vulnerability through the Wordfence Bug Bounty Program.
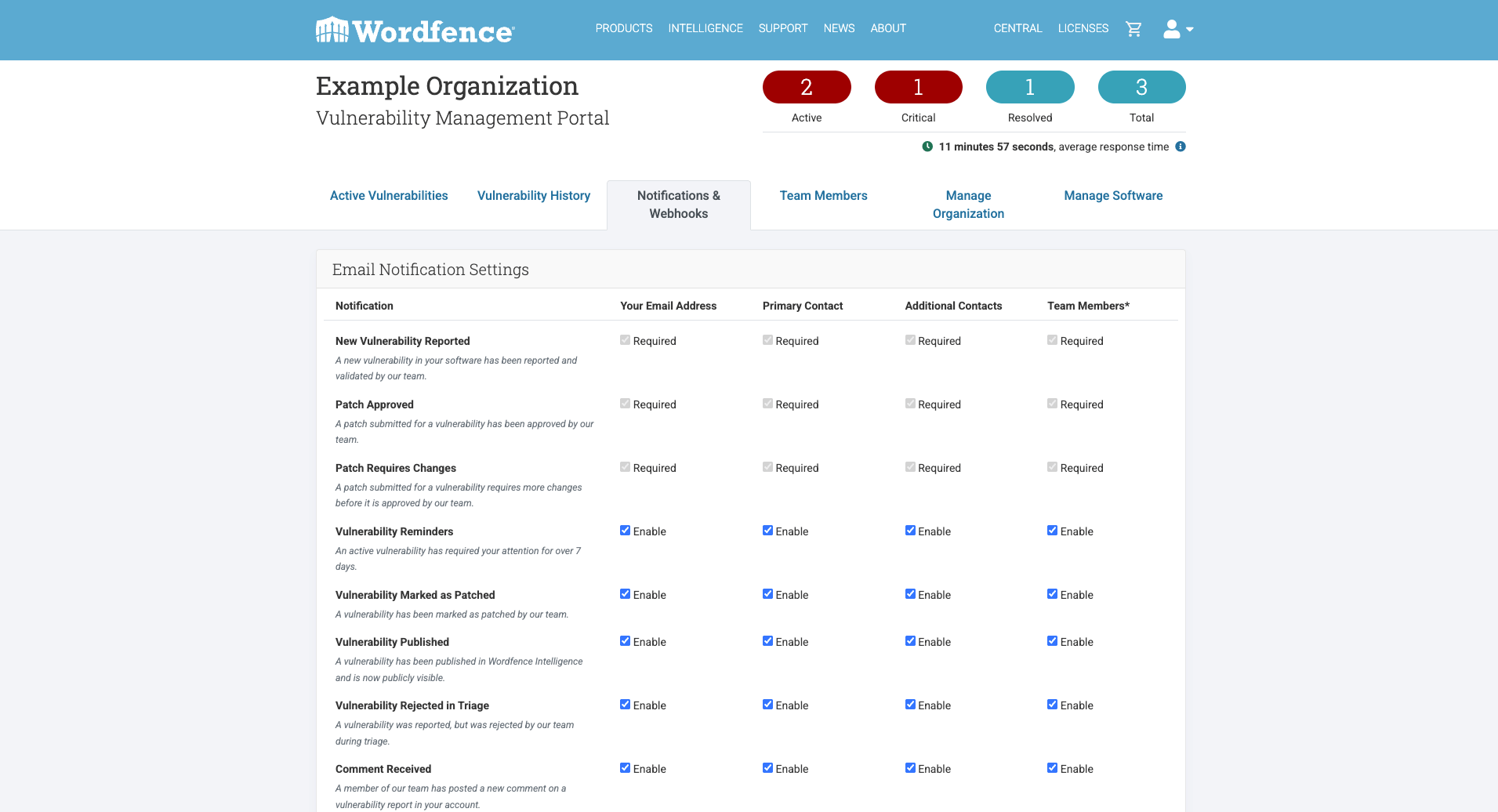
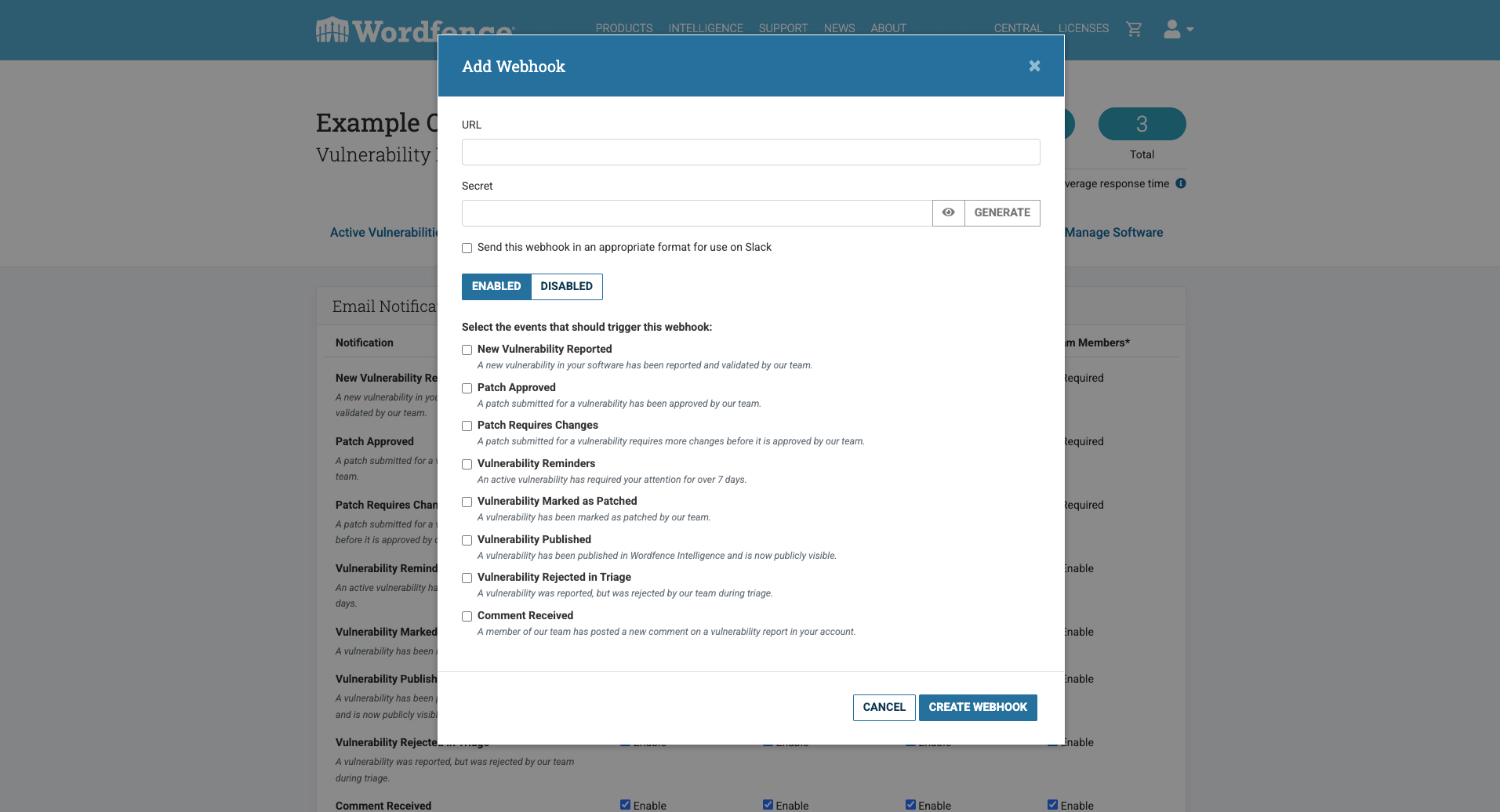
Customizable Vulnerability Notifications with Email and Webhook Options
Vendors gain complete control over their notification preferences with the vulnerability management portal, with the option to enable a webhook alongside email notifications.
This allows for seamless integration of alerts into their existing workflows. While certain critical notifications are mandatory, vendors retain the flexibility to customize who receives which notifications within their team.
Email Notifications Overview
Webhook Notification Overview
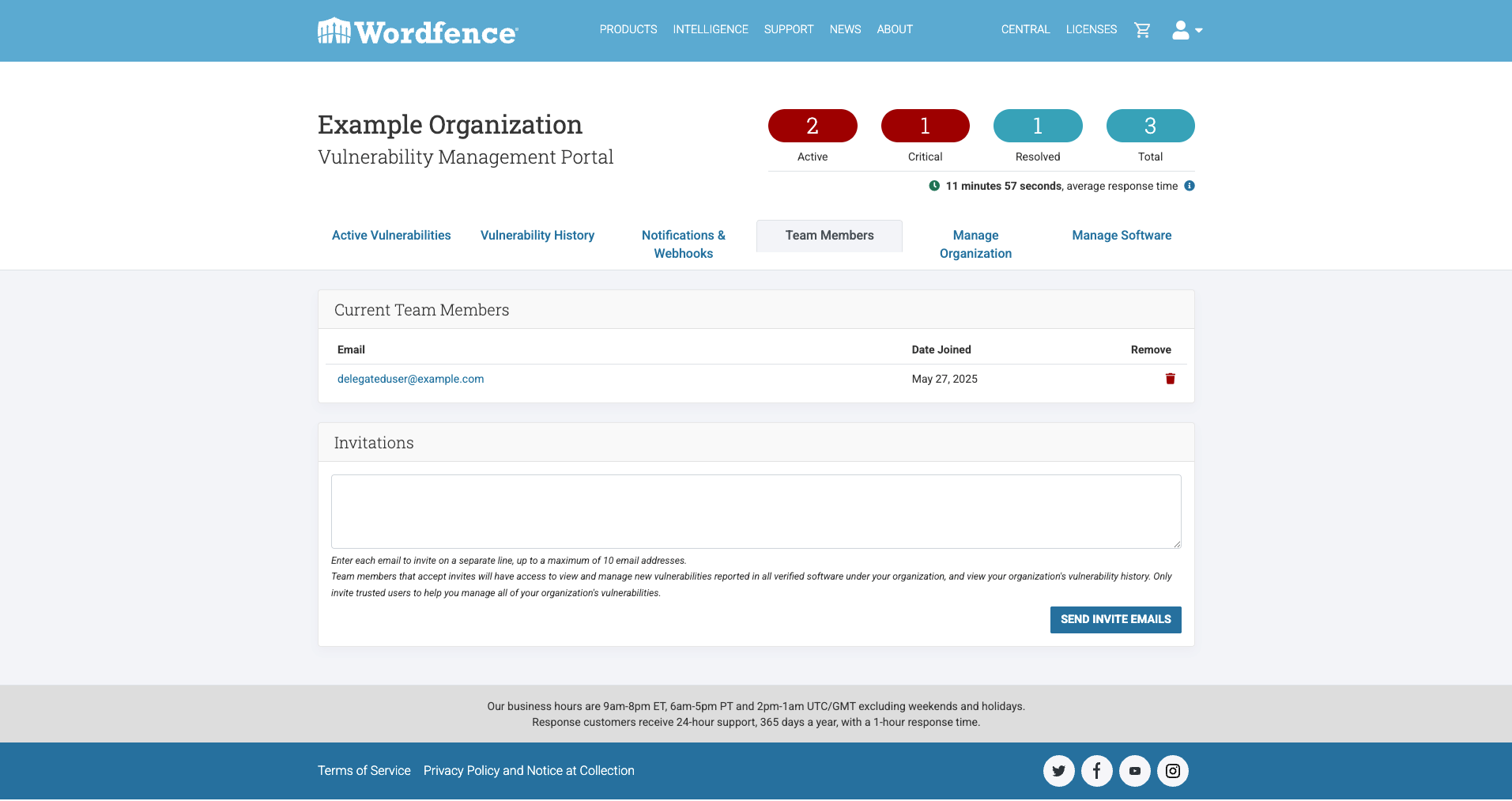
Delegated Team Member Access to Manage Vulnerability Reports
We recognize the complexities that arise when a single point of contact is responsible for handling all vulnerability reports, and we do not encourage the use of shared accounts. This can create a security weakness and often leads to bottlenecks, delayed responses, and an increased burden on one individual.
To address this critical challenge and streamline the vulnerability management process for our vendors, we ensured the portal launched with delegated access for team members.
This crucial feature empowers vendors to distribute the responsibility of vulnerability management across their internal teams. Specifically, vendors will have the capability to delegate access to as many as ten additional team members. Each of these designated team members will gain the ability to directly receive real-time vulnerability notifications, ensuring that critical information is disseminated promptly to all relevant parties.
Furthermore, they will have comprehensive access to view and action vulnerability reports, enabling a more collaborative and efficient approach to addressing security concerns. This delegation functionality is designed to foster a more resilient and responsive security posture for our vendors by ensuring that multiple qualified individuals can actively participate in the vulnerability resolution workflow.
Accessing the Wordfence Vulnerability Management Portal: Currently An Invite-Only Experience
The Wordfence Vulnerability Management Portal is currently operating on an exclusive, invite-only basis. This phased rollout ensures a controlled and effective onboarding process, allowing the Wordfence team to provide dedicated support and optimize the portal’s functionality before a wider release.
Receiving an Invitation
The primary method for gaining access is through a direct invitation from the Wordfence team. We are actively distributing invite codes to all recognized vendors who are partners in our shared mission of enhancing web security or have worked with us in the past on a vulnerability disclosure. These invitations are being sent out systematically to ensure comprehensive coverage of our vendor network. We also send out invites on any new vulnerabilities we disclose.
Requesting an Invite Code
If you are a vendor who has not yet received an invite code and would like to have access to the portal in this beta period, you can proactively request one through our dedicated online form located here:
https://www.wordfence.com/threat-intel/vendor/register#vendor-program-interest-form
This form is designed to gather basic information that allows our team to verify your vendor status and assess your eligibility for an invite.
Conclusion
The launch of the Wordfence Vulnerability Management Portal marks a significant advancement in the responsible disclosure of vulnerabilities within the WordPress ecosystem. By providing a free, centralized, and efficient platform, Wordfence continues to uphold its commitment to enhancing web security.
The rapid adoption by over 130 WordPress vendors covering over 640 individual plugins and themes underscores the critical need for such a solution, fostering a more collaborative and secure environment for all.
This initiative, with its detailed reporting, improved communication features, and flexible access, reinforces Wordfence’s dedication to protecting the WordPress community and its millions of users.
The post Revolutionizing Responsible Disclosure: Introducing the Wordfence Vulnerability Management Portal for WordPress Vendors appeared first on Wordfence.
